Information Security through Image Fusion
Information Security through Image Fusion
Price : 10000
Information Security through Image Fusion
Price : 10000
.svg)
Multiple images are fused into a single image with a technique 3-D Wavelet Transform in this many images are fused into a single image. A set of data had been embedded with a technique of LSB Matching to hide the data in the image by that information security is been provided. The steganography used to hide the information behind the image, audio and video. Most of the existing system used many techniques. In this paper, data hiding is been done by LSB matching technique, then the generated stegno image file to apply the image fusion. So it is very hard to find the original data from the image fusion. We can get very secured information by using this system.
1.1 INTRODUCTION
The Greek word “steganos” meaning covered writing is basically the concept behind the theory of steganography. Here it is difficult to even detect that a message is being sent. This type of ciphering called steganography, the ancient art of hiding messages sent undetectable. This methodology is gaining popularity with everyday passing because of its unique properties and those days are not far off when it would be adopted by armies of the world for secret message passing. The history of sending hidden message is very old. Greeks used it writing message on some material and later covering it with wax, tattooing messages on bald head, later growing hair to cover it up. In World War II invisible inks were used to write messages in between the lines of normal text message [1]. World War II saw the use of microdots by Germans. In microdots technology, photograph of secret message taken was reduced to size of a period. This technology was called “the enemy’s master piece of espionage” by FBI director J. Edgar Hoover. Normal and innocent messages carrying secret messages moved from one place to another.
There are currently three effective methods in applying Image Stegnography LSB Substitution, Blocking, and Palette Modification [2]. LSB (Least Significant Bit) Substitution is the process of modifying the least significant bit of the pixels of the carrier image. Blocking works by breaking up an image into “blocks” and using Discrete Cosine Transforms (DCT). Each block is broken into 64 DCT coefficients that approximate luminance and color—the values of which are modified for hiding messages. Palette Modification replaces the unused colors within an image’s color palette with colors that represent the hidden message.
We have chosen to implement LSB Substitution in my project because of its ubiquity among carrier formats and message types. With LSB Substitution we could easily change from Image Stegnography to Audio Stegnography and hide a zip archive instead of a text message. LSB Substitution lends itself to become a very powerful Steganography method with few limitations. LSB Substitution works by iterating through the pixels of an image and extracting the ARGB values. It then separates the color channels and gets the least significant bit. Meanwhile, it also iterates through the characters of the message setting the bit to its corresponding binary value.
PROCESS
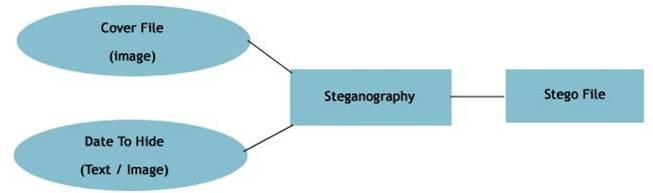
SYSTEM REQUIREMENTS
Ø MATLAB 2015 and with following tool boxes
o Image Processing
o Machine Learning
A CPU with minimum 4 GB ram and core i3 or above processor.
Windows 64bit
CONCLUSION
In this paper, information is highly secured by using image fusion in steganography. The proposed technique chops the data in 8 bits after the header and uses LSB to hide data from a pre defined position agreed between two parties. Same position is only used once to enhance security. After get the stegno file to apply to 3-D Wavelet Transform. A very important advantage of using 3-D WT image fusion over alternative image fusion algorithms is that it may be combined with other 3-D image processing algorithms working in the wavelet domain, such as ’smooth versus textured’ region segmentation where only a small part of all wavelet coefficients are preserved, and volume rendering [3, 51, where the volume rendering integral is approximated using multi resolution spaces. The integration of 3-D WT image fusion in the broader framework of 3-D WT image processing and visualization is the ultimate goal of the present study.